SSH Tunnel
SSH tunneling is the process of setting up an SSH connection and configuring that encrypted session to forward a port from one machine to another. This is handy if you need to, for example, use X11 forwarding on a server in the DMZ. This is accomplished by mapping a local host port to the remote server port. This guide is written as an example of setting up an SSH tunnel from your personal machine to a server within the DMZ, but the possibilities are endless.
Open a tunnel
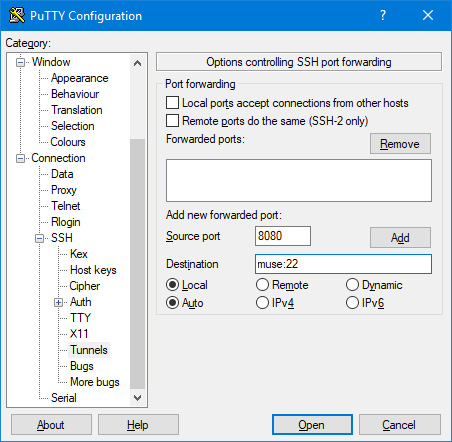
Open PuTTY and head to Connection -> SSH -> Tunnels.
- Source port is the port you'd like to use on your local machine. Select a port number that is not currently in use. Alternate ports and high number ports will work best for this. We'll use port 8080 here (HTTP's alternate port).
- Destination is the end point you're trying to map your local port to. For this example we'll use port 22 on muse.
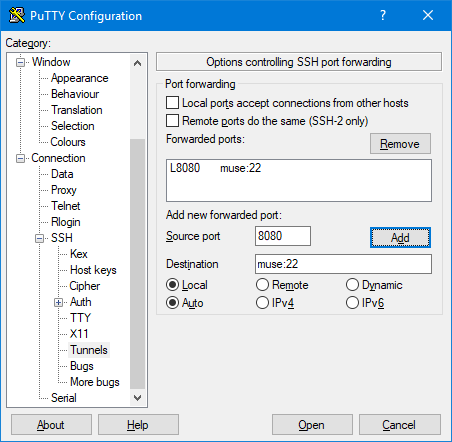
When you're happy with your selections, click add and you'll see it listed in the Forwarded ports box.
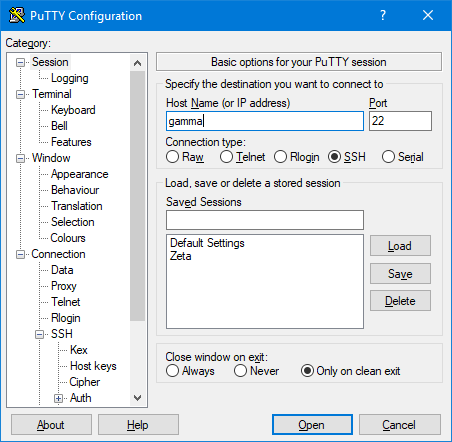
Now return to the Session options page and enter the host name or IP of the server you'd like to tunnel through. Because we're trying to tunnel to a server in the DMZ in this example, we need to connect to a server that can communicate behind the DMZ. Gamma is available for this, so we'll use that one.
When you click Open to start the connection, you may notice it looks like a standard PuTTY session. If you'd rather JUST open a tunnel and forgo the shell, the option is under Connection -> SSH -> Don't start a shell or command at all.
Congratulations, you're tunneling! This connection will remain active until the PuTTY session is closed.
Using the tunnel
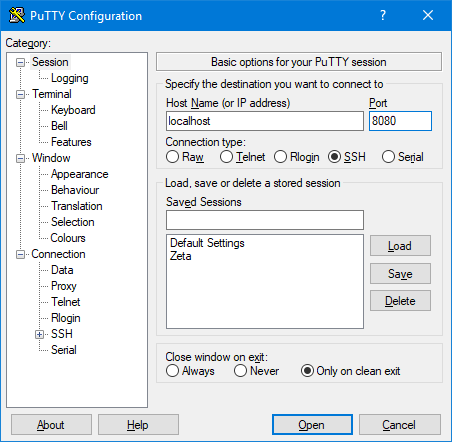
As mentioned earlier you've tunneled a remote port to your local machine. It may seem strange at first but to connect to the remote destination we must first... connect to ourselves. Open up a second PuTTY session and point it at the source port you selected earlier (8080 for our example). For the hostname, use localhost or 127.0.0.1.
Your natural first reaction is going to be that this is insanity and connecting to one's self would lead you nowhere. Ye of little faith...
The benefit of connecting this way is the traffic acts like it's a direct connection. You can't forward X11 through the DMZ to your computer - but you sure can tunnel it!
Notes
- This process isn't limited to SSH traffic. It will tunnel ANY traffic between two remote ports, and it will do so by wrapping that connection in SSH encryption, basically making this a one port VPN. If you need "direct" connectivity to a machine that can't be directly connected to or are otherwise worried about unsecure traffic in a hostile environment - SSH tunnels will always be your friend.
- If you kill the PuTTY window that's holding the ssh tunnel open while the connection is still in use, PuTTY will close the shell and halt with the window still open. Once you kill all connections using the tunnel, the PuTTY window will close on its own.
- If your PuTTY session gives you the error "X connection to localhost:10.0 broken (explicit kill or server shutdown)." make sure you're running a local X11 server, such as Xming.